10 ways to manage corporate data and personal data on personal devices (BYOD)
2024.05.14
10 ways to manage corporate data and personal data on personal devices (BYOD)

BYOD (Bring Your Own Device) means using your own mobile phone for work. By connecting to the organization’s network system or connecting to other organization software systems such as email, apps, and work files in various formats.
BYOD is becoming increasingly important in the business world, where approximately 90% of employees already use their own devices at work. (Even if used in a limited way) Most businesses Mixing BYOD devices with work will not be allowed. But there is also a belief that BYOD may help employees be more productive. However, if left unmanaged It may lead to information leakage. For example, if an employee uses a smartphone. his to access the company’s network. and later lost the said phone Confidential company information stored on the phone It may be read by someone who cannot be trusted. This raises the inevitable question: How do you ensure the security of your organization’s data? while helping employees work more efficiently
In this article, we present 10 ways to use BYOD to create a more efficient, secure and private workforce.
1. Create your policy before procuring technology / Set clear regulations
Compliance, privacy, security, approved apps, etc. must be clearly stated in the Acceptable Usage Agreement (AUA) or End User License Agreement (EULA). This should be in simple language. that every employee can easily understand as they must sign before starting to use the equipment If your device is lost or stolen, make sure you have clear instructions on how to handle it. In order to prevent problems that follow.
In this BYOD era, policies or regulations must be documented. and enforce it through a Unified Endpoint Management (UEM) solution so that IT teams can call remotely. And automatic enforcement can be performed as soon as an employee starts turning on a new phone, tablet, or laptop. Here are some things to consider when setting your own policy.
— Devices : What types of devices are smartphones, tablets, laptops or wearables?
— Compliance : What regulations must your organization comply with, such as the Health Insurance Portability and Accountability Act (HIPAA), the Health Information Technology for Economic and Clinical Health (HITECH) Act, the Financial Industry Regulatory Authority (FINRA), or the European Union’s General? Data Protection Regulation (GDPR), make sure you understand how these regulations relate to your BYOD.
— Security : What security measures are required? Password and or multi-factor authentication Encryption, Jailbreak/root detection, Malware protection Access conditions These are things to consider.
— Apps : whitelist for approved apps or blacklist apps that are not allowed. How can apps be deployed to various devices in the organization (such as smartphones, tablets, or laptops) without interrupting employee work?
— Agreements : Is there an acceptable usage agreement (AUA) in case employees use their personal mobile phones for work?
— Corporate access : What information can employees access through their mobile devices? Email, calendar, contacts, File shares, documents, repositories, Intranet sites, Wi-Fi networks, VPN.
— User privacy : You must protect the privacy of your employees. What personal data is collected from employee devices? What personal data will remain untouched? How do you communicate so that the organization understands?
— Data plans : Who supports the data service fees incurred? The organization or the employee.
2. Find the devices that are accessing corporate resources / determine the devices that will access information
Know which devices have access to corporate data. Unified endpoint management (UEM) technology helps you manage all types of devices on a single platform: laptops, desktops, smartphones, tablets, wearables, and Internet of Things (IoT) devices
3. Make enrollment simple / accessible and easy to use
Samsung Knox Mobile Enrollment (KME), Google Android Enterprise Zero-touch enrollment, or Apple Device Enrollment Program (DEP) make enrollment easy, such as employees doing self-enroll or IT teams doing bulk enrollment.
4. Configure your devices over-the-air / Easy modification
Over-the-air or OTA is one of the amazing features available in mobile technology. Once enrollment is complete, UEM sends required profiles, credentials and settings to the employee’s phone over-the-air or OTA.
— Email, contacts and calendar
— VPN, Wi-Fi profiles
— Corporate content
— Internal, public apps
— Security policies (e.g., container)
5. Help your users help themselves / Users can access the basic system by themselves.
Users can solve basic problems with the Self-service platform without having to wait for the help desk or IT to come in and handle it through the UEM system that will provide basic convenience.
— Initiate PIN, password resets
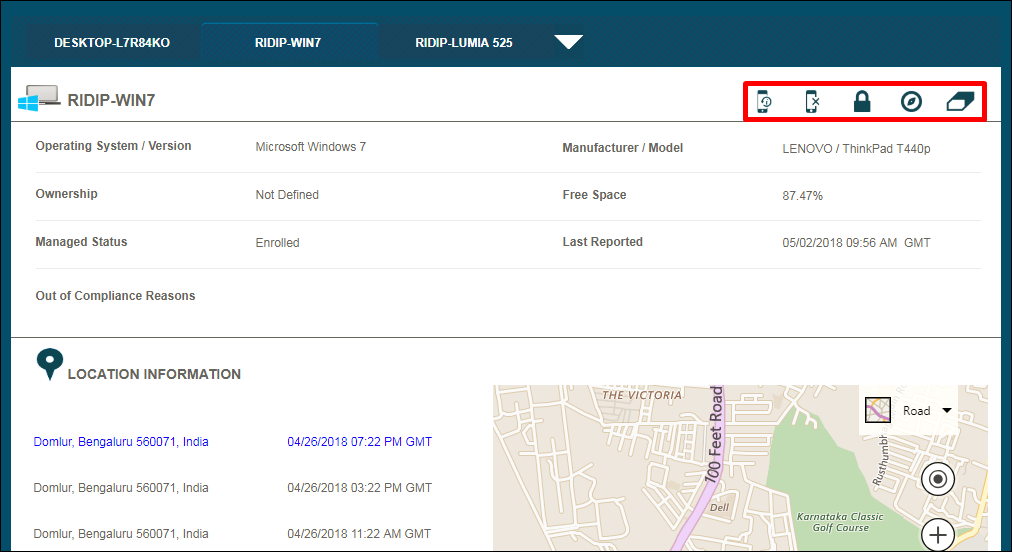
— Geo-locate a lost device with an interactive map
— Wipe a device remotely
6. Protect the privacy of your users / Protect privacy information
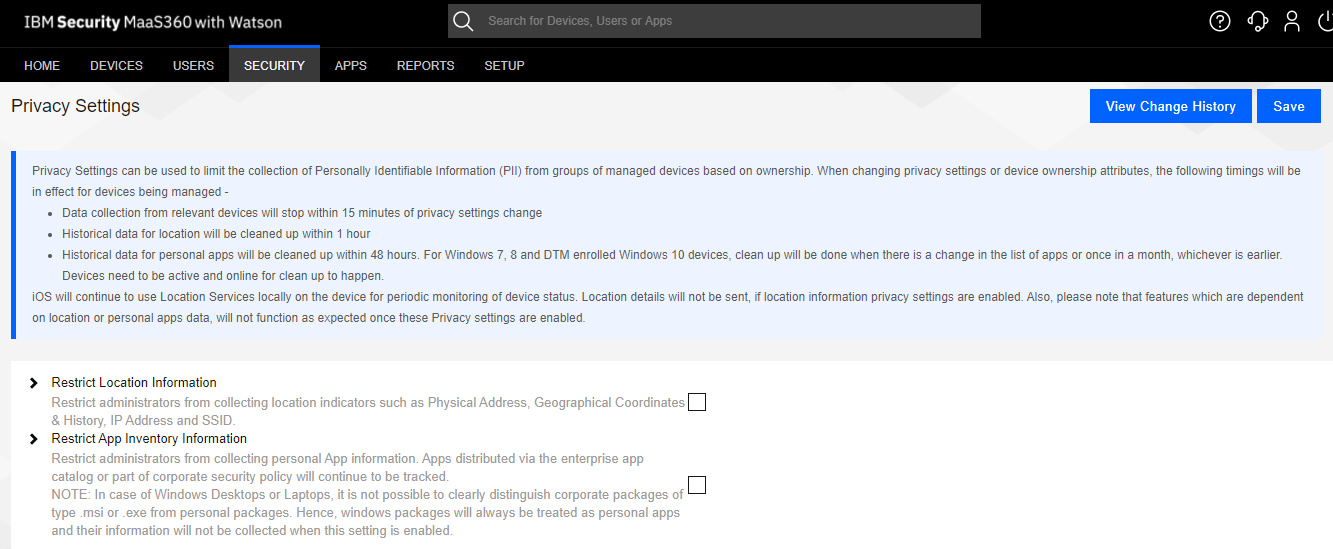
Personally, identifiable information (PII) is a set of data that can be used to identify, contact, or locate an individual. international privacy law And many localities have emerged to prevent agencies from collecting this information.
The privacy policy should be clearly communicated to employees about what information is stored. And what information is not collected from their mobile phones?
— Personal emails, contacts, calendars
— Location, Photos
— App data, Text messages, Call history, Voicemails
— Usernames, Passwords
A good UEM solution can help block these accesses and help companies meet PII regulations to prevent breaches of employee privacy. and increase peace of mind for employees, for example:
Prevent access to user personal information
Unable to access user’s location.
7. Keep personal information separate from corporate data / Keep personal and corporate information separate.
Corporate apps, work files, and other data must be secured by IT if an employee leaves the organization. and cannot access or touch employees’ personal emails, apps, and photos With this management, a Unified endpoint management (UEM) solution can help you with Encrypted container sandbox for corporate resources.

8. Manage data usage / Manage data usage
Whether it is an employer or an employee, you will pay the monthly mobile service fee. But you might also want to help users track their data usage and educate them about the benefits of using Wi-Fi. You can set limits on roaming data usage. And automatic Wi-Fi profiling ensures that devices automatically connect to Wi-Fi while at company locations.
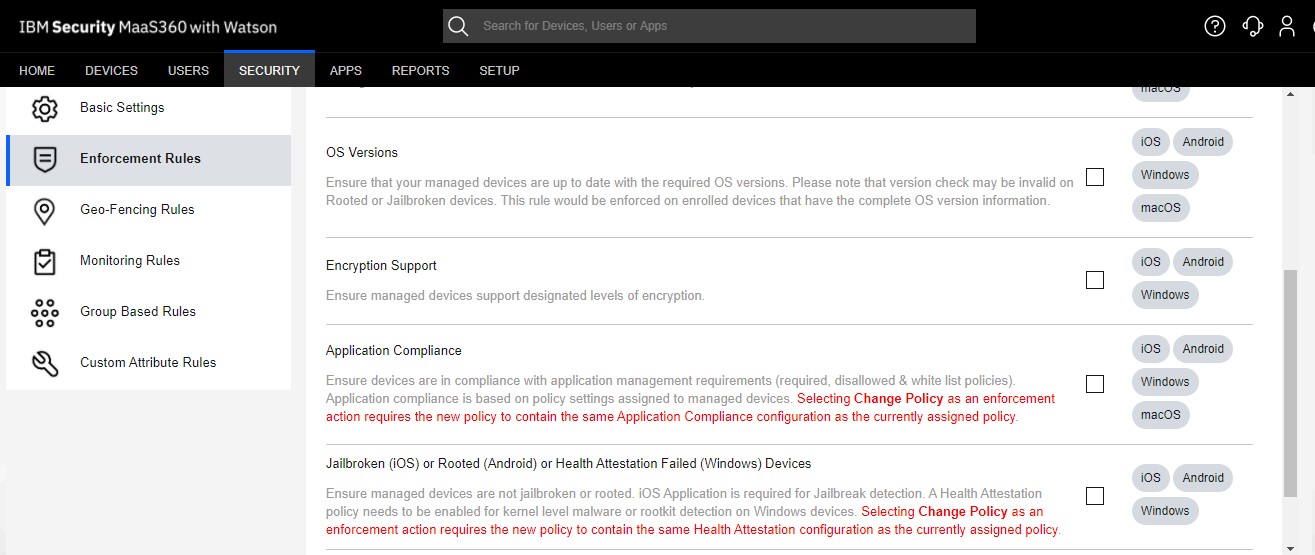
9. Continually monitor enrolled devices for noncompliance / can track connections to the system and violations of rules
To enforce the organization’s security policy and reduce security vulnerabilities You should require monitoring. Violation of security policy Here are some of the most common problems that your UEM monitor can detect.
– Users can try removing MDM from their device. Your UEM should detect it. and immediately restrict access to corporate data
– To avoid the limitations of the operating system (OS), sometimes employees jailbreak (Apple iOS) or root (Google Android) their mobile phones. To open the door to downloading various pirated apps This opens the door for malware that can steal data. If the device is jailbroken or rooted, the UEM solution should be able to detect it. and take automated responses, such as selectively wiping corporate apps and sensitive data from the device immediately.
– Setting the minimum OS version helps ensure that every mobile phone will work at its full potential. and security vulnerabilities, your UEM should be able to keep the OS version up-to-date.
10. Measure the benefit from BYOD / Benefits from using BYOD
The benefits of BYOD aside from reducing the cost of acquiring new mobile phones It also helps improve the work efficiency of employees. It allows employees to work from outside the office. It also helps reduce employees’ errors in their work. Because they are familiar with their own equipment It is also lightweight, easy to carry and can be used outside such as meetings and selling work to customers. or an emergency occurs, such as unfavorable weather conditions Transportation problems, power outages, and various unexpected events. If employees can work off-site, it will be beneficial to the business.
Example when comparing investing in purchasing mobile phones for employees with using BYOD
BYOD
– Monthly telephone service charges are paid by the employee or in part y the company.
– Cut the budget for purchasing mobile phones.
– Cost of UEM
Corporate-owned model
– Budget for each device
– Monthly telephone service budget
– The budget for the destruction of property has expired.
– Warranty
– Time and IT labor to manage
บทความที่เกี่ยวข้อง

ความปลอดภัย
บริการใหม่
Work from Home ปลอดภัยด้วย Wizberry Laptop Management
💼 Work from Home อย่างมั่นใจ ด้วย Wizberry Laptop Management บนแพลตฟอร์ม IBM MaaS360 🔒 ในยุคดิจิทัลที่การทำงานจากที่บ้าน (Work from Home) กลายเป็นสิ่งจำเป็นมากกว่าทางเลือก ความปลอดภัยของอุปกรณ์พกพา โดยเฉพาะ Laptop ของพนักงาน จึงกลายเป็นหัวใจสำคัญที่ทุกองค์กรไม่อาจมองข้าม แม้พนักงานจะไม่ได้อยู่ภายในสำนักงาน องค์กรก็ยังต้องมั่นใจว่าอุปกรณ์ที่ใช้เข้าถึงข้อมูลสำคัญ ยังคงได้รับการดูแล ป้องกัน และควบคุมอย่างเหมาะสม เพื่อป้องกัน การรั่วไหลของข้อมูล, ภัยคุกคามทางไซเบอร์, และ ความเสียหายทางธุรกิจ นั่นคือเหตุผลที่โซลูชัน Wizberry Laptop Management สำหรับ IBM MaaS360 ถูกพัฒนาขึ้นมา — เพื่อช่วยให้องค์กรสามารถจัดการและควบคุมความปลอดภัยของอุปกรณ์ทั้งหมดได้แบบ ครบวงจร และจากระยะไกล
2025.04.10
ข่าว
ความปลอดภัย
Oracle แจ้งลูกค้าหลังเกิดเหตุ Data Breach ทำให้ข้อมูลหลุดจากระบบ Cloud
Oracle แจ้งลูกค้าหลังเกิดเหตุ Data Breach ทำให้ข้อมูลหลุดจากระบบ Cloud
2025.04.10

ข่าว
ความปลอดภัย
มัลแวร์มือถือที่กำหนดเป้าหมายธนาคารในอินเดียทำให้ผู้ใช้กว่า 50,000 รายเสี่ยงต่อการถูกโจมตี
การโจมตีอุปกรณ์เคลื่อนที่ขนาดใหญ่ นักวิจัยของ zLabs วิเคราะห์ตัวอย่างมัลแวร์เกือบ 900 ตัวอย่างและพบความพยายามร่วมกันในการใช้ประโยชน์จากอุปกรณ์ Android มัลแวร์ซึ่งจัดอยู่ในประเภทโทรจันของธนาคาร ปลอมตัวเป็นแอปธนาคารหรือแอปของรัฐบาลที่ถูกกฎหมายและแพร่กระจายผ่าน WhatsApp ในรูปแบบไฟล์ APK เมื่อติดตั้งแล้ว มัลแวร์จะขอข้อมูลที่ละเอียดอ่อน
2025.03.14
